Attack paths move through unmanaged identities, not the identities IAM tools are watching.


Incident Response Teams
Respond to Identity Threats at the Speed of Attack.
Attackers don’t wait for IAM coverage. Orchid gives incident responders identity observability across unmanaged systems, where breaches often begin.
The Problem
Most incidents start with identity.
Stolen credentials, orphaned accounts, or service access no one monitors.
When identity lives outside IAM, responders lose time reconstructing access paths instead of stopping threats. Orchid provides immediate visibility and explainability into identity behavior across every application and identity.

The Identity Visibility Gap During Incidents
Authentication and authorization behavior inside apps is invisible, slowing investigation and response.
Non-human/ Machine identities lack ownership and telemetry, making attribution and containment harder under pressure.
How Orchid Aligns Identity with Incident Response
Discover
Continuously discover every application and identity across cloud, on-prem, legacy, and custom environments.
Analyze
Understand all authentication and authorization activity, across every application to map attack paths.
Orchestrate
Push identity context into IR and SOC workflows for faster response.
Audit
Preserve identity evidence for post-incident review reporting and increased security posture.

Key Features
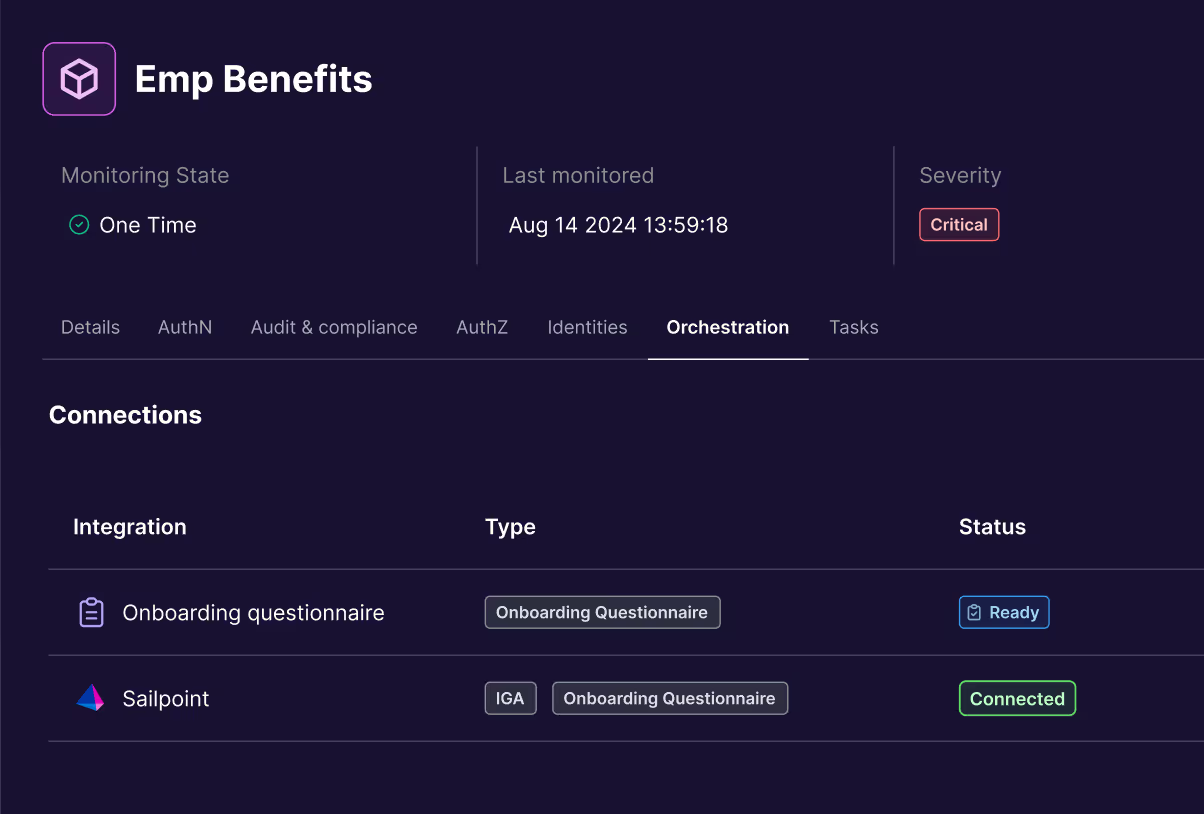
Infrastructure-wide Observability
See every application and account throughout the organization

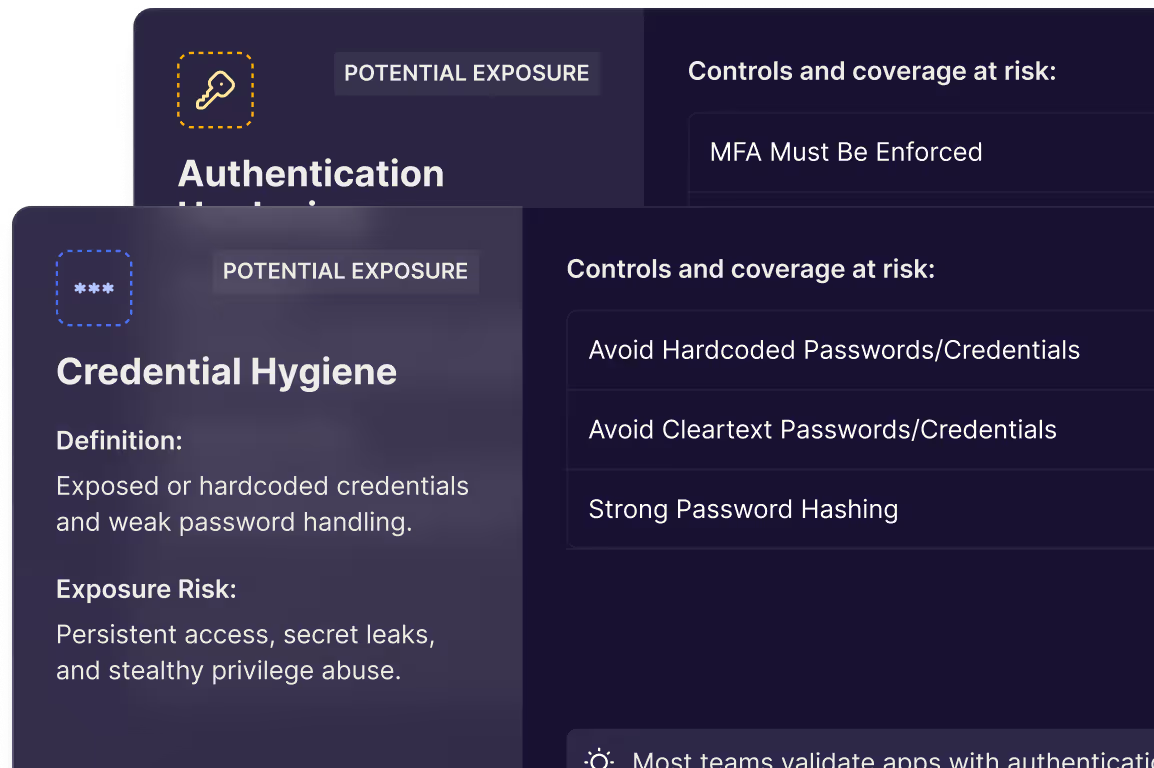
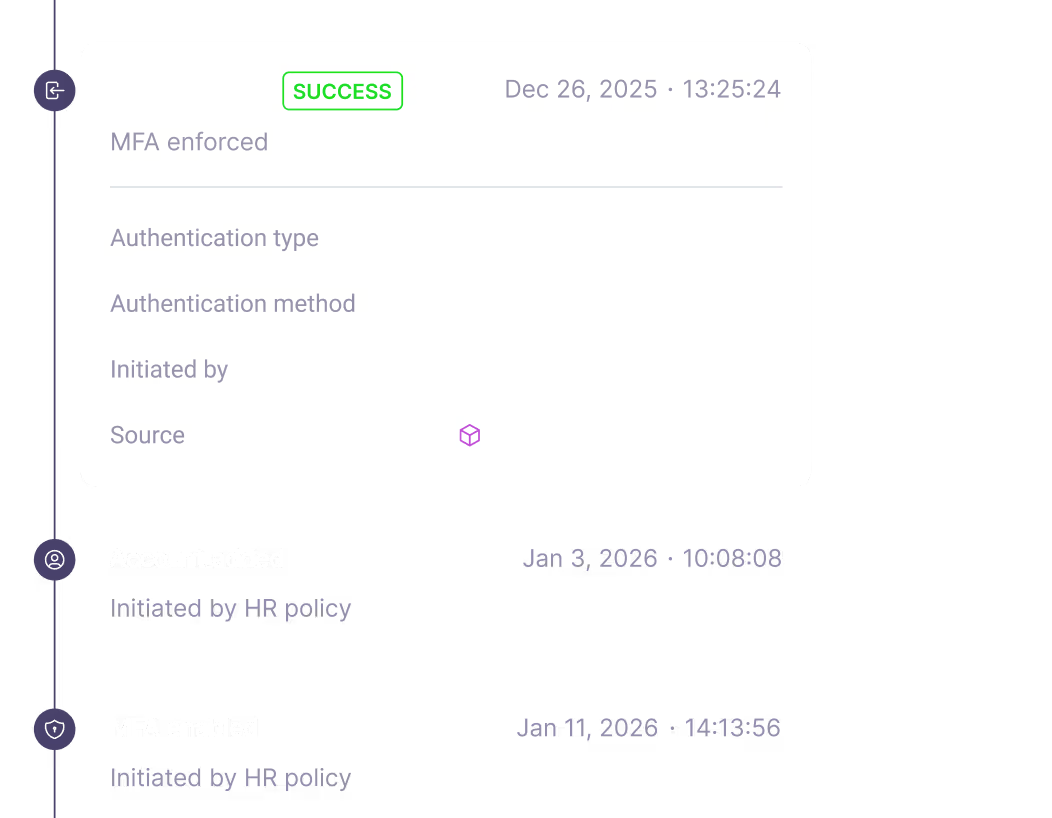
Identity Activity Audit
Track utilization of credentials to find initial entry and lateral movement

IAM Orchestration
Decommission all instances of compromised credentials, with proof


Why this Matters
Threat actors log in more than they hack in.
Without visibility into unmanaged identities, attackers move unnoticed. Orchid exposes identity behavior in real time, turning hidden access into actionable insight during incidents.

What Our Customers Are Saying
“With user credentials serving as the #1 entry method of threat actors, identity is the new perimeter.”
Costco
Jon Raper

Outcome
Faster incident response.
Confident containment and remediation.
Lower exposure to future identity-related attacks.

See Orchid
In Action Today
Maintain strong and consistent posture across all self-hosted and SaaS applications.




