
Overview
Organization: A large multinational financial services firm (“FinSrvCo”) operating a broad and complex application estate: on-premises data centers (45%, multiple cloud providers including AWS and Azure (43%), and software-as-a-service (12%)
Challenge: The security operations center (SOC) detected a likely cyber security incident involving unauthorized access and lateral movement. Historically, FinSrvCo’s Mean Time to Containment (MTTC) averaged ~48 hours, representing significant exposure even after detection. Delays were primarily due to the difficulty of visualizing all identity flows - particularly unmanaged service accounts, non-human identities, and unmanaged, AD disconnected, applications outside central IAM oversight- in order to determine credentials used in the incident as well as the scope of that use.
Solution Requirements: To accelerate incident response and confidently remediate, FinSrvCo turned to Orchid for comprehensive visibility into identity flows and continuous auditing of identity activity in order to:
- Correlate a suspected host with its associated application
- Map authentication and authorization flows (who, what, where) available to the unauthorized party
- Extend audit coverage by combining unmanaged app logs with managed app and IAM system logs (who, what, where, when)
- Correlate identity activities into timelines to accelerate detection of risky patterns
- Confidently decommission compromised identities across applications and identity flows using DB analysis or authoritative data sources
- Deliver contextual dashboards with actionable insights, highlighting at-risk identities and surfacing orphan, local, and dormant accounts with activity trails for incident responders
Key Components of Orchid Visibility Usage
- Authentication & Authorization Flow Mapping: End-to-end visibility into human, non-human, service account, managed, and unmanaged identity flows, including effective permissions and potential access paths.
- Audit Generation (Managed & Unmanaged Apps): Creation of consistent audit logs for managed and unmanaged apps not entirely covered by the IAM stack.
- Audit Collection (Managed Apps & IAM Stack): Ingestion and normalization of identity audit data from IdPs, PAM, IGA, and IAM systems.
- Centralized Activity Timeline: A single correlated record of all identity activities across the enterprise, human and machine, making audit, investigation, and compliance reporting dramatically easier.
- Real-Time Insights & Correlation: Immediate detection of risks like risky login sources, unexpected identity propagation, and service account usage spikes. Lateral movement detection was strengthened by aligning identity audit trails with suspicious flows into the lateral movement patterns across different servers and applications.
- Blast Radius Dashboards: Clear visualization of which applications a compromised identity could reach, enabling IR teams to prioritize containment actions precisely.
Incident Description
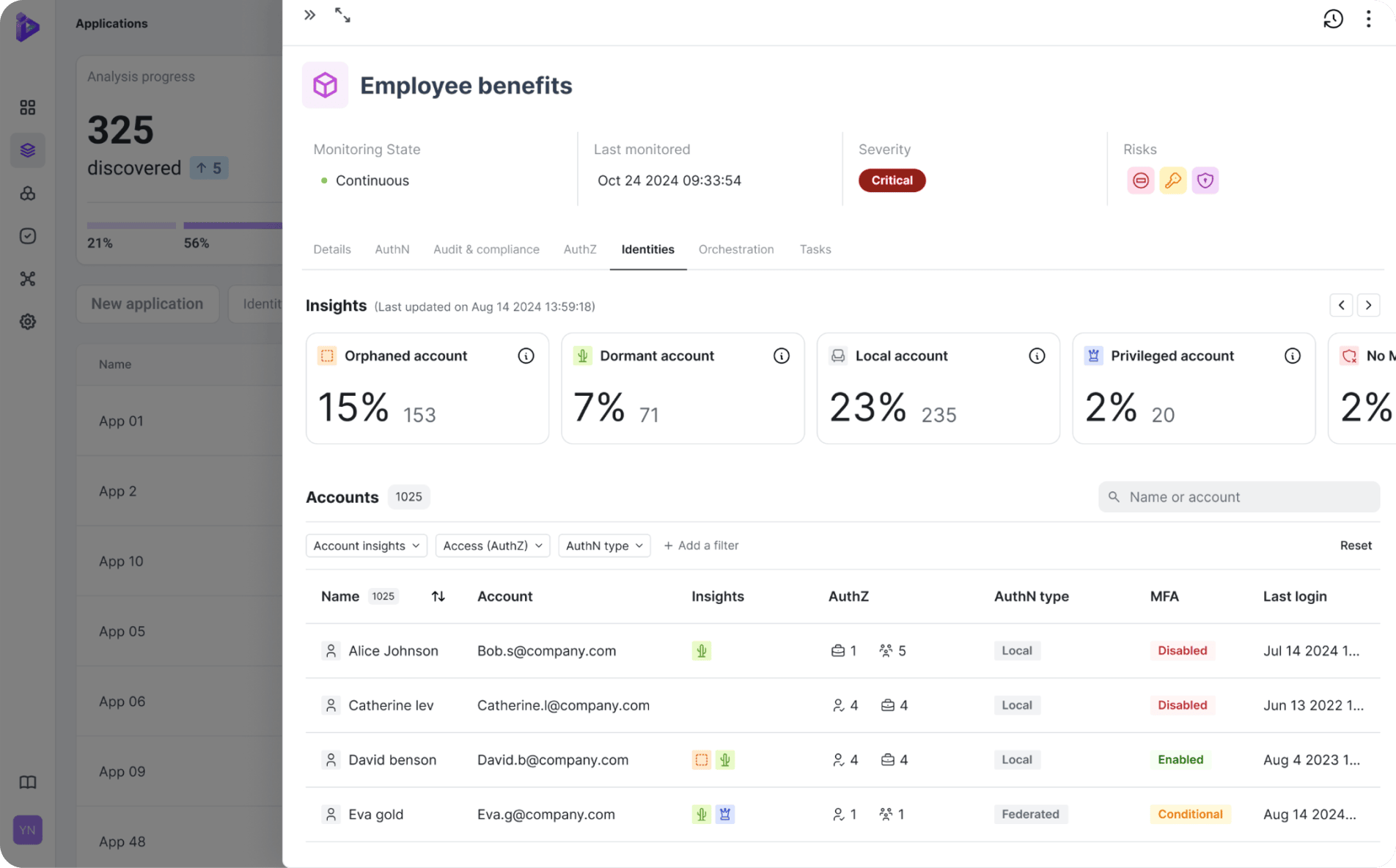
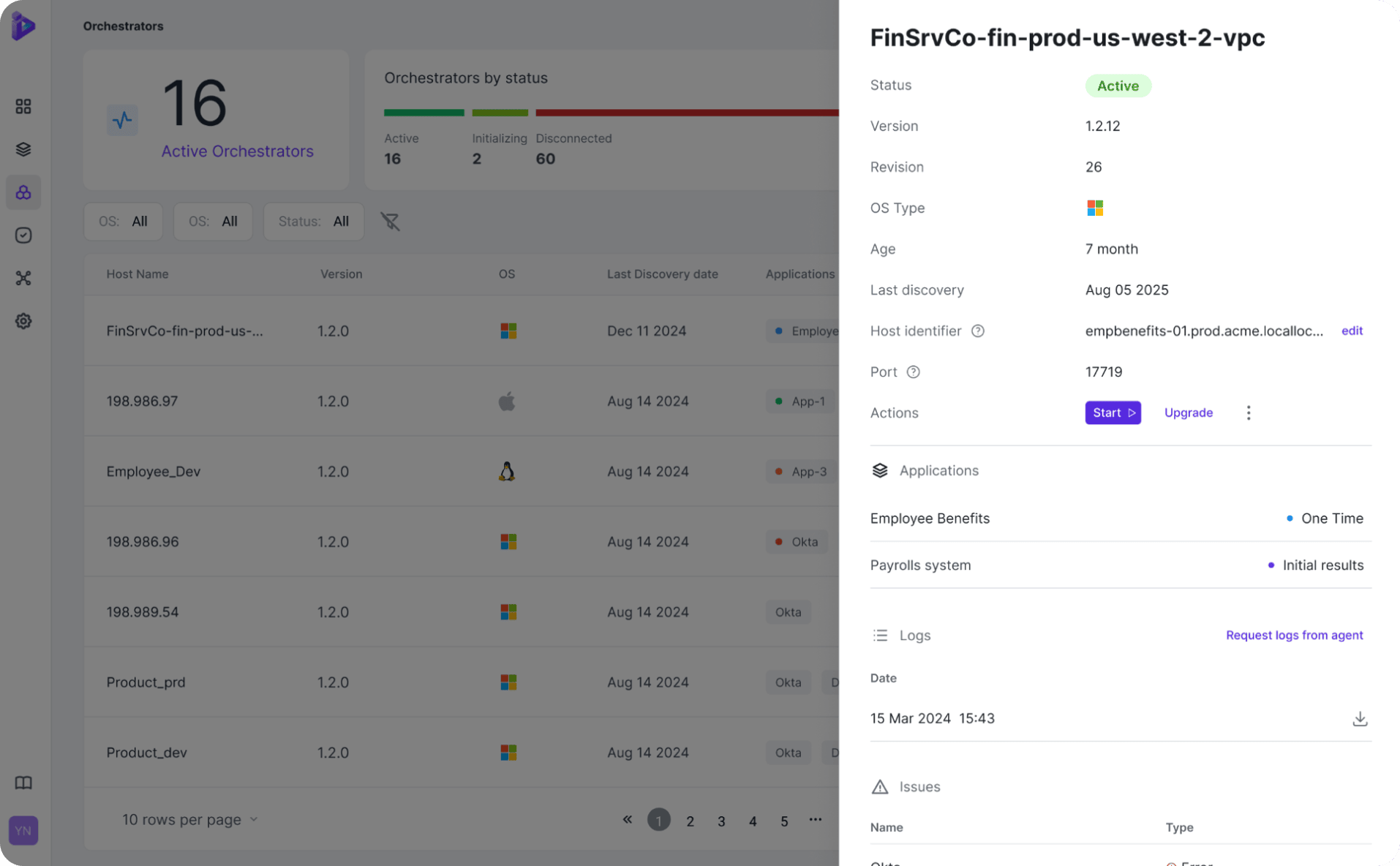
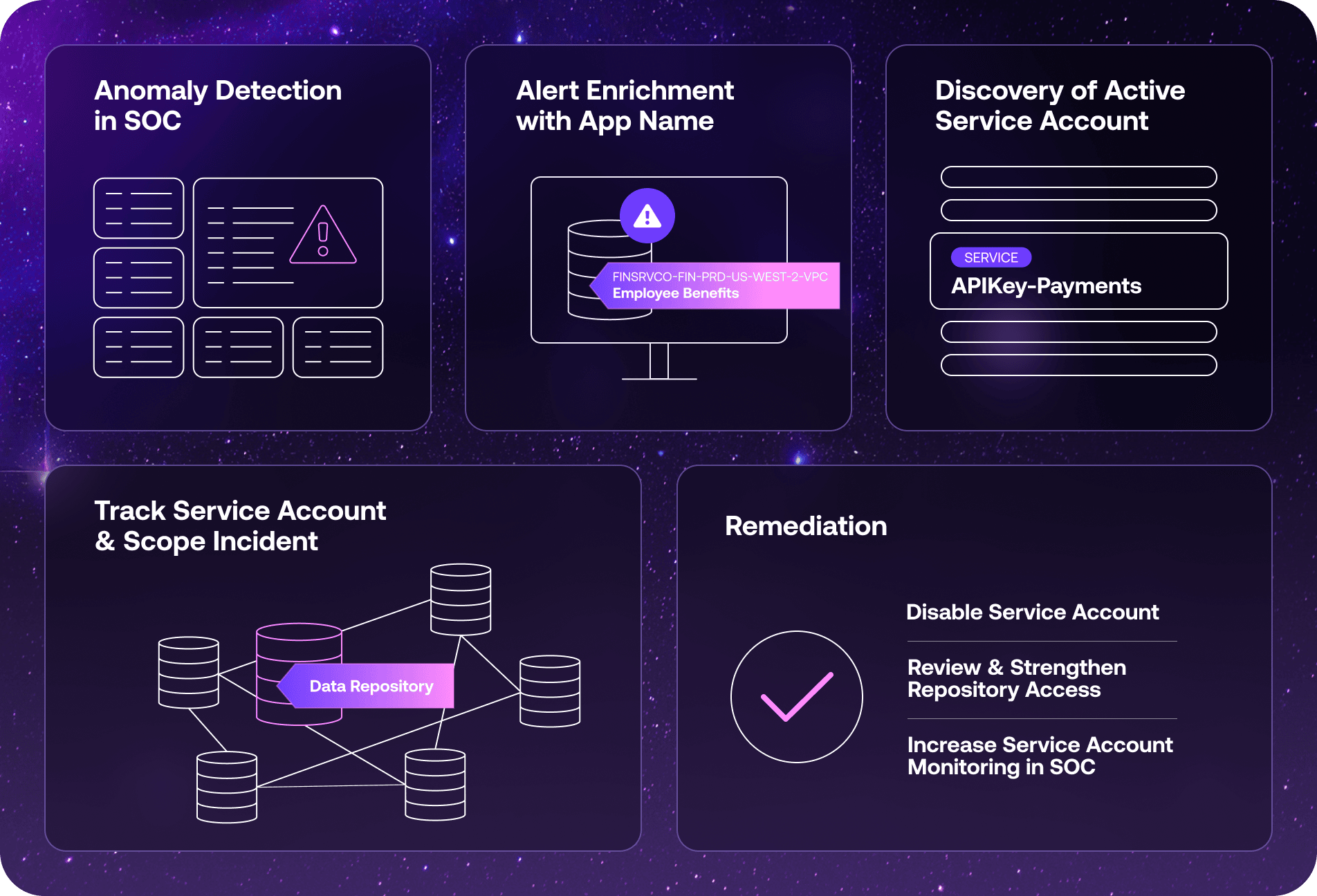
Late morning, SOC monitoring flagged unusual bandwidth activity from an AWS asset named FinSrvCo-fin-prod-us-west-2-vpc. Using the insight available in the CMDB, previously populated by Orchid’s application discovery and base analysis, the IR team quickly correlated this asset (and activity) with hosted applications and determined it was running ‘Employee-Benefits’.
Further analysis of host activity logs showed a concerning downstream access pattern: a service account named ‘APIKey-Payments’ from the ‘Employee-Benefits’ application was connecting to a sensitive internal data repository.
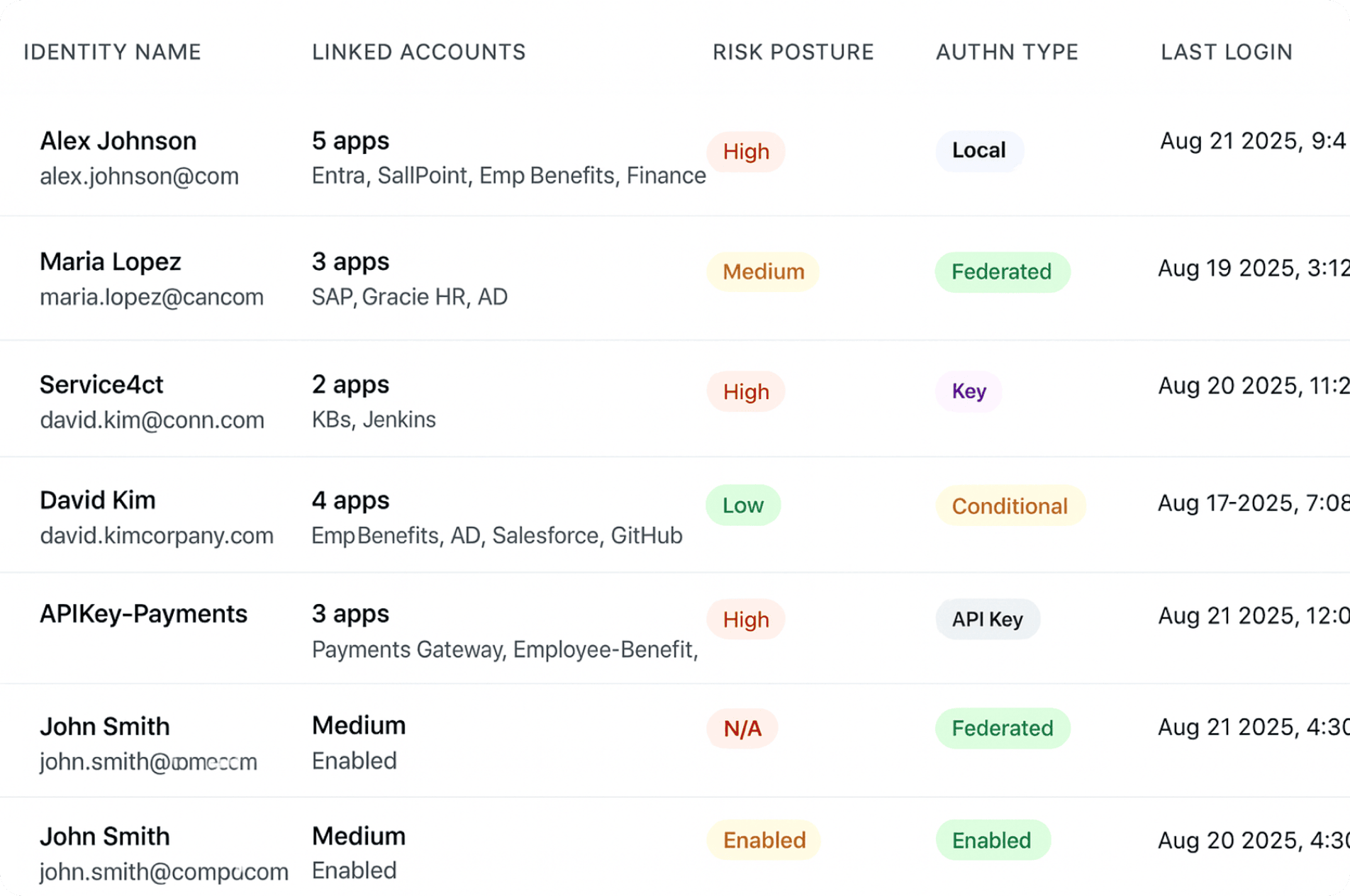
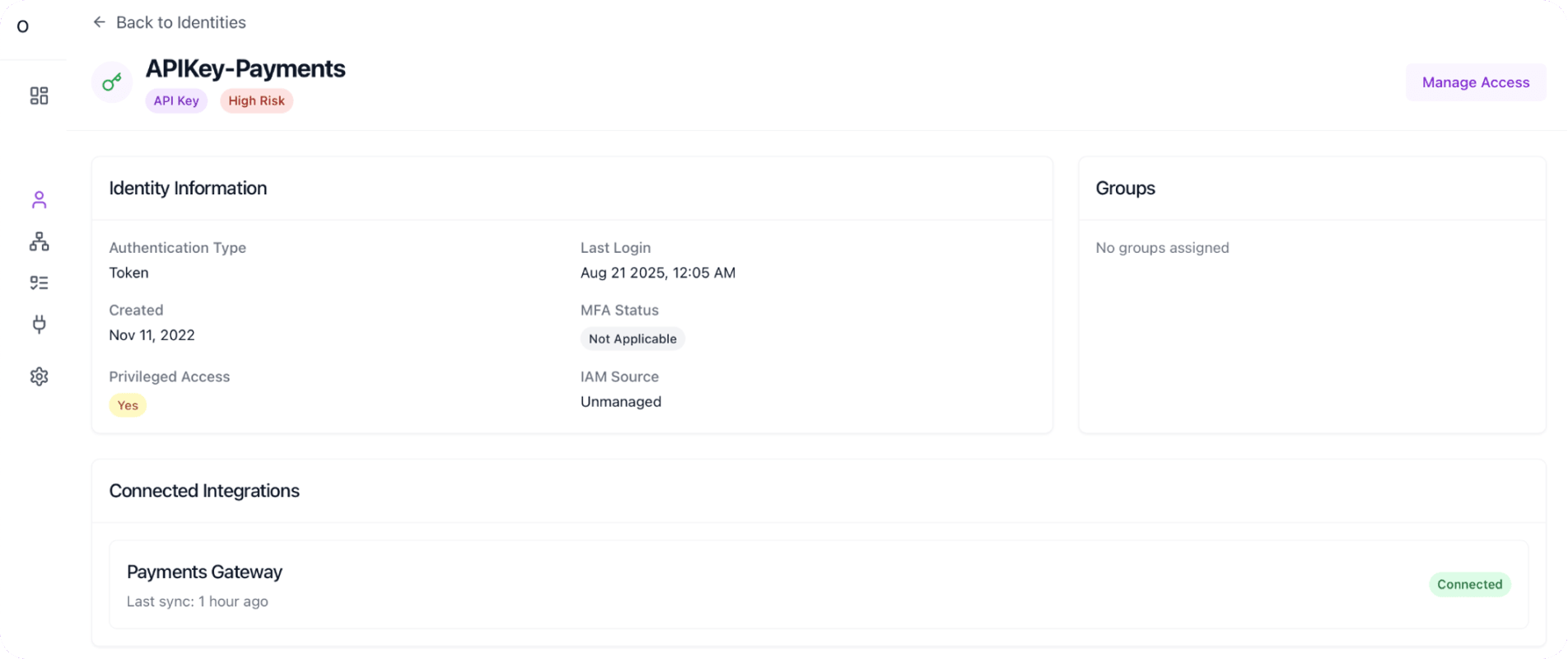
By auditing the service account in Orchid’s identity view, the SOC team uncovered the real threat: an attacker had stolen the service account credentials and was using them to pivot laterally within the environment.
SOC & IR Team Actions
- Alert Triage
- The SOC initially observed an anomalous bandwidth and escalated the issue to IR.
- Orchid provided immediate context by mapping the AWS asset ‘FinSrvCo-fin-prod-us-west-2-vpc’ to the relevant application ‘Employee Benefits’.
- Correlation & Investigation
- Using the Orchid Visibility audit for app ‘Employee Benefits’ revealed that the suspicious activity wasn’t just network noise, but a service account labeled ‘APIKey-Payments’ establishing repeated connections to a sensitive repository.
- By searching for the service account ‘APIKey-Payments’ and its audit trail across the entire application estate, the IR team confirmed lateral movement through compromised credentials and gained business context on the exfiltrated target data.
- Containment & Response
- The exposed service account was disabled, and credentials were rotated.
- Repository permissions were reviewed and restricted.
- Monitoring policies were updated to detect anomalous service account usage from cloud-hosted applications.
Impact / Risk Assessment
- Immediate Risk: Unauthorized access to sensitive internal data repositories.
- Lateral Movement Risk: Attacker leveraging cloud-hosted application accounts to extend access into internal systems.
- Business Risk: Potential compromise of critical data and further spread into production infrastructure if left unchecked.
Before Orchid (Historical Baseline)
- Detection: ~12 hours (network anomaly rule).
- Investigation: Mapping the compromised service account’s permissions across multiple managed and unmanaged applications required ~24 hours, leveraging PAM and directory systems with support from SecDevOps due to the account being unmanaged service, and often relying on spreadsheets, manual documentation, and tribal DevOps knowledge. (Even so, uncertainty remained as to what unmanaged applications may have been compromised.)
- Containment: Trial and error elimination utilizing network segmentation, broad system lockdowns, large-scale credential resets using extensive manual forensics, all took ~48 hours in total. (However, the organization remains uncertain the stolen credentials were decommissioned in all applications / authentication paths in every application.)
With Orchid Identity Visibility
- Detection: Within ~9 minutes. Orchid flagged risky identity activity behavior in real time.
- Impact Assessment: Dashboards revealed the full blast radius of the compromised service account, applications, data stores, and systems exposed.
- Action Plan:
- Disable the compromised service account via orchestrated response.
- Block associated network privileges with Zero Trust policy changes.
- Rotate credentials and provision least-privilege replacements for affected services.
- Validate if exfiltration occurred by analyzing correlated audit logs.
- Containment: Completed within ~3 hours, nearly 95% faster than the historical time.
- Confidence: Evidence-based confirmation of scope (both where credentials were used and where they were not) and remediation (both where credentials had been enabled and the fact that they were disabled or not authorized to begin with.)

Result: By leveraging Orchid Visibility’s focus on authentication/authorization flows, audit generation and collection, and correlated insights, FinSrvCo cut containment time by +90% and transformed a complex, high-risk breach into a manageable, auditable incident.
Resolution
- Compromised credentials revoked and rotated.
- Service account access reviewed, with privileges reduced to the minimum required.
- Orchid’s audit data integrated into FinSrvCo SIEM platform.
- SOC detection rules enhanced to flag anomalous account activity.
- Additional monitoring placed on AWS assets to correlate app-to-data repository connections in real time.

Understanding, let alone maintaining, identity security posture across any large organization- with its diverse and always evolving application estate- is a constant challenge.
Remember, that estate includes applications created by different developers, at different times- when technology, regulations and cyber risk were different- and even by different organizations if acquisitions were part of the growth strategy.
Any approach, but especially an automated one, that provides a comprehensive and accurate view into the true state of identity, is hugely valuable to CISOs. Especially when it can surface all of the identity flows coded in each application. We know that many threat actors are adept at finding the alternate or forgotten ways into our organizations, and this report highlights the most common exposures we need to look out for (and address).
The insights shared here are instructive for every cyber security professional.
- 48%
Storage of hard coded, cleartext credentials or use weak hashing
- 44%
Authentication paths that bypass the corporate Identity Provider
- 40%
A lack of baseline controls like rate limiting, account lockout and password complexity
- 37%
Outdated or non-standard authentication protocols
- 37%
of applications failed to enforce access controls fully or at all
Checklist to Identify the Top Missing Identity Controls
Download Checklist
Discovery and Gap Analysis: Continuous Visibility Beyond the Known
Orchid delivers continuous, telemetry-driven visibility into identity implementations across all automatically discovered applications regardless of geography, technology stack, or existing compliance knowledge. This capability empowers organizations to uncover both commonly missed controls and hidden identity mechanisms that conventional audits and reviews often fail to detect.
No Prior Context or Manual Input Required
Unlike traditional assessment and onboarding processes that rely on interviews, documentation, or involvement from app owners or developers, Orchid's analysis is entirely autonomous. It requires no prior data points, tribal knowledge, or manual onboarding, making it ideal for large, fast-changing environments.
Save Time, Save Money — Harness Your True Identity Landscape
By eliminating the need for human-led discovery, context-gathering, or code walkthroughs, Orchid significantly reduces the time and cost of identity posture management. It accelerates both discovery, gap analysis and remediation cycles including onboarding, freeing up security teams and engineering resources to focus on higher-impact work while utilizing the organizational siloed identity tools.
Checklist, Fully Covered
Our platform aligns directly with the Checklist to Identify the Top Missing Identity Controls and many more providing instant, actionable insights on where your applications stand and what needs attention.
- January 2025
PowerSchool Breach
Cybercriminals reportedly used stolen credentials to access a support portal that lacked MFA, exposing sensitive student and parent data.
- March 2025
Jaguar Land Rover Incident
A threat actor used stolen credentials to infiltrate the company’s Jira system, allegedly stealing over 700 internal documents.
- April 2025
Verizon Data Breach Investigations Report
Verizon Identifies Stolen Credentials as Top Breach Entry Point In their latest report









