When we first talked about adding audit capability to the Orchid offering, it felt… practical. Necessary, even. But not always emotional.
As a PM, you hear “audit” and you think about checklists. Reports. Timelines. Helping teams get through a painful process a little faster. That was the headspace.
Then the work started.
We sat with design partners. We went inside real environments. We looked at thousands of applications, not slides, not diagrams, not how things were supposed to work, but how they actually did.
And that’s where the tone changed.
Identity activity was everywhere. Inside application code. Inside custom auth flows. Inside service accounts no one remembered creating. Behavior that never touched centralized IAM, yet still showed up during audits. Still mattered during incidents. Still got referenced in board decks.
And then there were the details that really stuck.
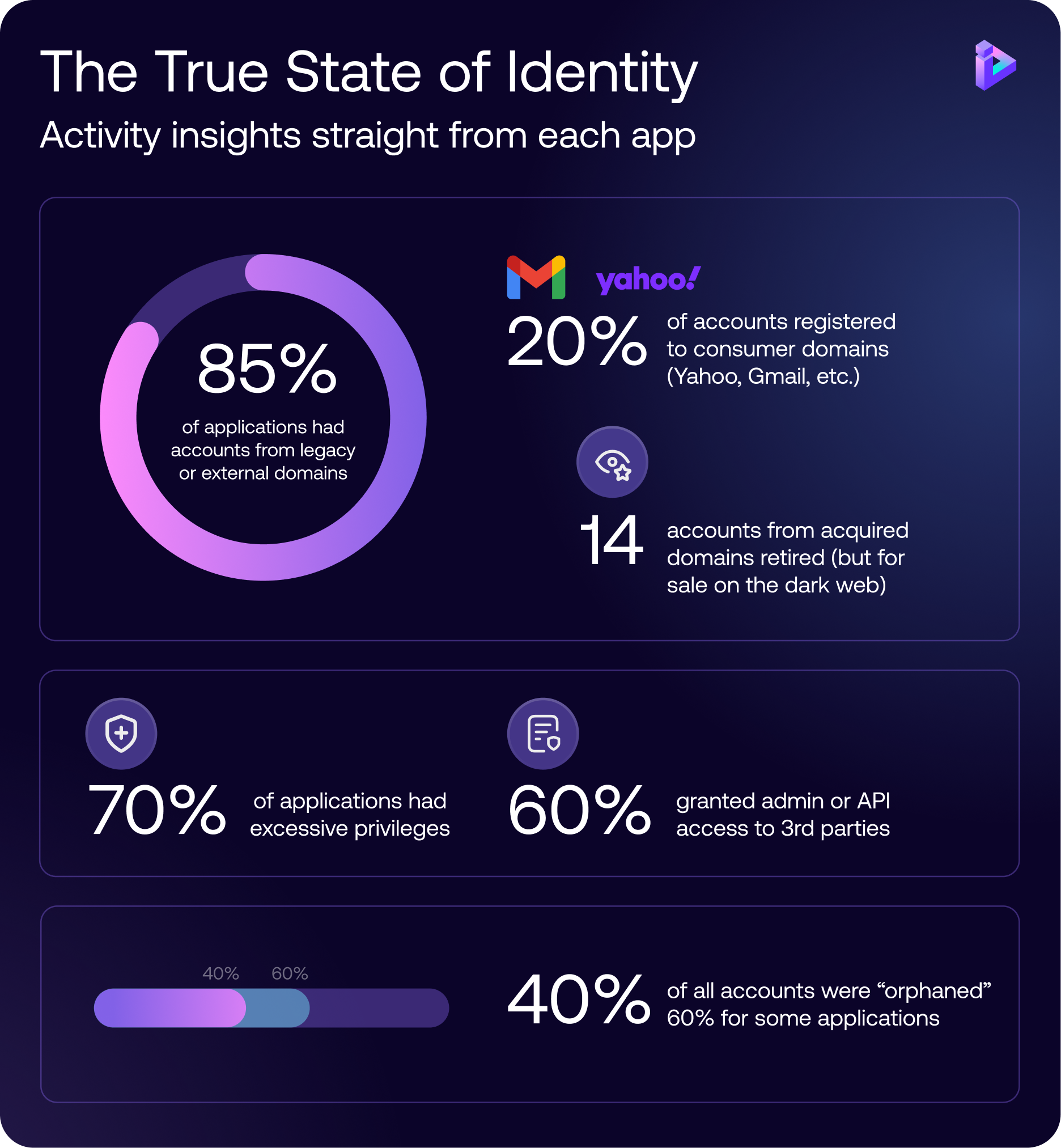
Third-party accounts with admin access that no one could fully explain.
Accounts tied to old or unexpected domains.
Applications where most everyone was a privileged user, for no apparent reason.
Email addresses with subtle misspellings. One character off. Easy to miss. Hard to justify. Still active. Still authenticating.
Some of them might be mistakes.
Some might be abandoned.
Some might be worse.
All of them were flying under the radar.
As an IAM practitioner, it hit close to home. We’ve all been in that moment. An auditor asks a fair question. A security leader asks for confidence. And the answer we give is inferred or ambiguous. Based on integrations. Based on policy. Based on what should be true. Not what is.
The audit data we uncovered made that impossible to ignore. Nearly half of identity activity sitting outside centralized visibility. Orphaned accounts lingering across applications, tied to domains long since retired. Privileges granted long ago and never revisited. External access accumulating quietly, without friction, without ownership. None of it is loud. All of it is risky.
That’s when our thinking shifted.
This wasn’t about helping teams prepare for audits. It was about enabling them to stop guessing. We stopped treating identity as configuration and started treating it as behavior. Something that happens. Something observable. Something you can prove. Not just where IAM is wired in. But even where it isn’t. Not just what policies say. But what identities actually do.
Identity Audit came out of that shift.
It looks directly inside applications and accounts. Managed and unmanaged. Human and non-human. It watches identity activity as it unfolds. Logins. Privilege use. Accounts that sit quietly long after they should have been removed. Not to replace IAM tooling. To complete the picture. What surprised me most wasn’t how much we uncovered. It was how familiar it felt. These weren’t edge cases. They were the things teams have been working around for years, because they didn’t have another option.
Identity dark matter isn’t abstract. It’s the app never onboarded. The access no one remembers approving. The account that doesn’t quite match. The third party that never rolled off. The risk that stays invisible because it lives just outside the model.
As a PM, I’m proud we shipped this.
As someone who’s had to answer uncomfortable questions with incomplete data, I’m relieved it exists. Because identity decisions are only as good as the data behind them. And for too long, we’ve been making high-stakes calls with half the story. Identity Audit is our way of seeing the whole picture, and taking informed action.




.png)
.png)



.jpg)

.png)

.png)
.png)





