VoidLink Malware: The Identity and Visibility Implications
Recently, researchers disclosed VoidLink, a sophisticated, cloud-native Linux malware framework. While much of the analysis focuses on its evasion capabilities, the framework’s architecture highlights a critical aspect of how attackers target cloud environments: they prioritize identity theft, and infrastructure mapping over simple destruction.
Here is an analysis of the threat from an identity security perspective and why application visibility is the primary defense.
Overview of the VoidLink Framework
VoidLink is a modular malware framework explicitly designed for modern cloud infrastructure. Written in multiple programming languages, including Go, Zig, and C, VoidLink operates as a "cloud-first" implant that can detect the specific environment it inhabits, whether it is an AWS instance, a Docker container, or a Kubernetes pod.
The framework utilizes a plugin-based architecture similar to Cobalt Strike, allowing it to load specific capabilities dynamically. It balances operational security with functionality, using adaptive stealth mechanisms to evade EDR solutions based on the security products it detects on the host.

Persistence Through Identity Theft
Unlike traditional malware that relies solely on OS functionality for persistence, VoidLink leverages Non-Human Identities (NHIs) that can be found within the targeted environment to maintain long-term access.
The framework includes dedicated plugins designed to harvest credentials from the compromised environment. Within the environment, it can target different types of NHIs in the following forms:
- Cloud Metadata: Querying instance metadata APIs (AWS, Azure, GCP) to extract temporary credentials that are associated with IAM roles.
- CI/CD Secrets: Scraping environment variables and Git configurations for API keys and tokens.
- SSH Keys: Collecting private keys to facilitate lateral movement and persistence.
Exfiltrating these valid credentials increases the likelihood that the attackers can access the environment legitimately, even after the malware binary itself is detected and removed.
The Visibility Blind Spot
A critical capability of VoidLink is its ability to perform detailed reconnaissance of the victim's application landscape. VoidLink enumerates running processes, services, and container configurations to map the target's infrastructure.
This creates a dangerous asymmetry: the attacker often has better visibility into the running applications than the victim.
The effectiveness of credential harvesting attacks like VoidLink is amplified by common misconfigurations in how organizations store secrets. Many applications store database passwords, API keys, and other sensitive credentials in encrypted form within configuration files or codebases. However, when both the encrypted credential and the decryption key exist in the same location - whether in the codebase, configuration files, or environment variables - this transforms encryption from a security control into mere obfuscation. Automated harvesting tools can systematically defeat this protection by scraping application files, identifying encrypted credentials, locating the decryption routine, and executing the decryption logic to obtain plaintext credentials. This creates a false sense of protection while leaving credentials fully accessible to any attacker with file system access.
If an organization lacks a complete inventory of its cloud-native applications, remediation becomes ineffective. Security teams may remove the malware but fail to address the shadow applications or unmanaged services that were discovered and exploited by the attacker. Without visibility, the attack surface remains open.
Mitigating the Threat
Defense against frameworks like VoidLink requires shifting focus from endpoint protection to Application and Identity visibility.
Identity security platforms could counter this threat by providing a comprehensive, automated map of all running applications and their associated identities.
- Preventative Discovery: Identify key identity exposures, including unmanaged applications, over-privileged service accounts, weakly protected local credentials, and highly privileged, long-lived secrets and misconfigurations, before they can be targeted and exploited.
- Proactive Access Control: Deploy stronger authentication methods, improve secrets management, and establish continuous identity monitoring within the Security Operations Center (SOC) to actively mitigate the theft and exploitation of non-human identities.
- Effective Remediation: Upon detection of a threat such as VoidLink, an immediate response is necessary. This response should include tying affected credentials to their associated applications, focusing the subsequent investigation on those applications, and swiftly decommissioning the compromised credentials. However, organizations need to map not just "what was stolen" but "what can this stolen identity access?" Without understanding the full scope of permissions and cross-account trust relationships, security teams cannot accurately assess the scope of impact of a compromise.
- Security Telemetry Collection: Post-infection evidence collection from compromised hosts is unreliable due to modern malware's anti-forensics capabilities. Continuous, real-time host telemetry must be forwarded to a centralized Security Information and Event Management (SIEM) system. A comprehensive collection of login audit logs is critical for effective incident response and forensic analysis.
To effectively counter cloud-native attacks, organizations need visibility into their applications and identities that is equal to or greater than the visibility leveraged by the attackers.
Additional Analysis
As mentioned in other reports, VoidLink utilizes a plugin-based architecture.
While most of the modules have been covered in depth by Check Point and Sysdig, we wanted to take a deeper look at how attackers use credential harvesting to maintain persistence.
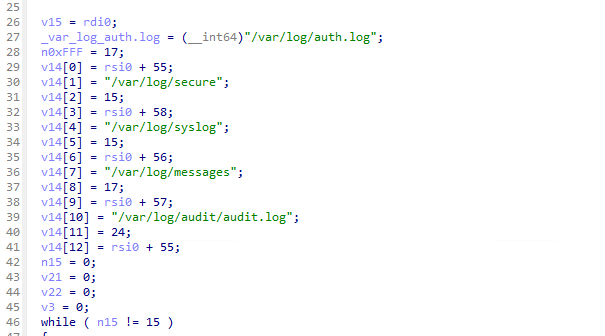
Credential Harvesting
In one of the samples, there were Zig’s debug symbols, and we can clearly see the credential harvesting module functions:
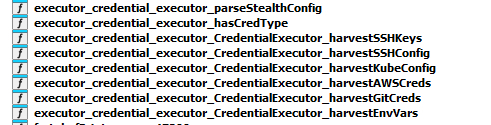
The functionality in this case is straightforward - search for files that contain credentials in known paths in the file system, e.g ~/.kube/config, ~/.ssh/id_rsa, or environment variables that might contain secrets, e.g AWS_ACCESS_KEY and AWS_SECRET .
Kubernetes Token Stealing
VoidLink implements the capability to detect whether it is running in a Kubernetes environment.
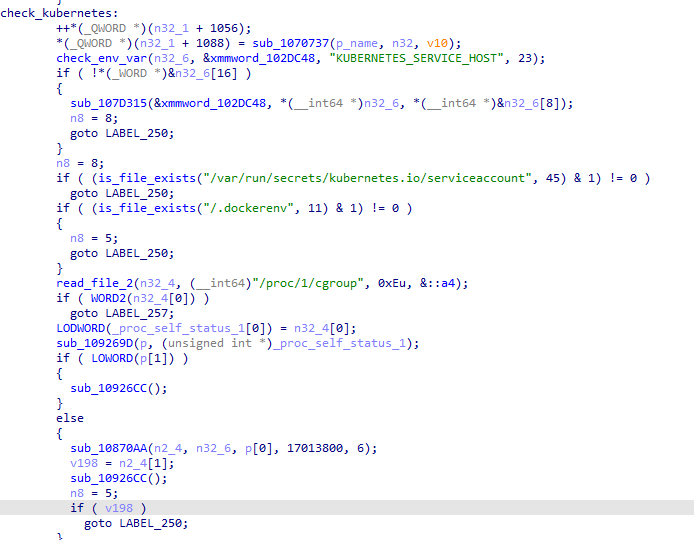
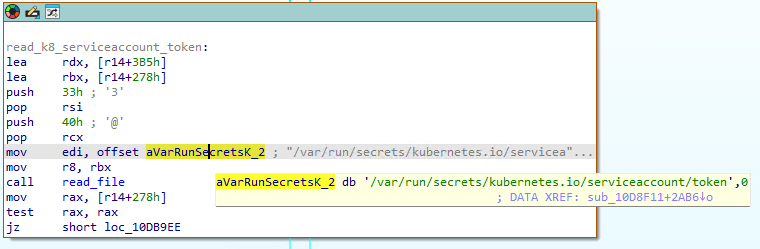
When VoidLink detects that it is running in a Kubernetes pod, it attempts to steal the pod’s service account token from /var/run/secrets/kubernetes.io/serviceaccount/token:
Evidence Removal
As mentioned in other reports, VoidLink has rootkit capabilities through a unique LKM (Loadable Kernel Module)-loading approach.
These capabilities allow it to remain hidden from basic analysis tools, such as process list checks or netstat.
In addition to these capabilities, we also observed that VoidLink attempts to remove specific files during evidence wiping.
As these files might assist SOC and IR teams in detecting and analyzing the attack later, VoidLink attempts to remove them.
The concept of evidence removal in malware isn’t new, and it’s a great example of why security teams can’t rely on extracting evidence from infected machines directly after infection.
Real-time auditing that syncs with a security product such as a SIEM should also be implemented, in case the malware on the infected machine has removed evidence of the attack.
Conclusion
While the industry has developed mature solutions for malware detection, with EDR and XDR platforms becoming standard for identifying malicious binaries like VoidLink, a critical gap remains in the post-exploitation phase.
Detecting the intrusion is only half the battle. Once an attacker has successfully executed code, even for a moment, the immediate priority shifts to assessing the impact of the stolen credentials. For many organizations, this remains a blind spot. Without a clear map of which applications hold which permissions, security teams cannot accurately determine the blast radius of a stolen identity or rotate the correct secrets.
This is one of the gaps Orchid Security addresses. By providing total visibility into the application layer and its associated non-human identities, Orchid ensures that when a compromise occurs, organizations can see exactly which identities have been compromised and revoke access effectively. In a landscape where malware is designed to steal identity, visibility is the only way to ensure resilience.
Indicators of Compromise
File Hashes


.png)

.png)
.png)




.jpg)