Audit Playbook: Continuous Application Inventory Reporting

Purpose
Auditors require verifiable proof of who accessed what, when, and why across all applications subject to compliance mandates.
Traditional IAM/IGA tools cover only managed apps, leaving unmanaged, on-prem, and shadow applications invisible. Orchid uniquely discovers in-scope applications, evaluates their identity controls, and generates continuous, compliance-mapped evidence.
Key Findings
01 Preparation
Before audits begin, enterprises need full visibility of their application and identity landscape. Without preparation, audits turn into firefights. Orchid lays the foundation with continuous discovery, established baselines, and clear ownership.
- Define audit scope and relevant frameworks (PCI DSS 4.0, HIPAA, ISO 27001, NIS2, FedRAMP, SOX).
- Enable continuous application discovery across managed (Entra, Okta, SailPoint, Workday) and unmanaged apps.
- Establish baseline metrics and dashboards for application inventory and identity posture.
- Assign audit ownership roles (Compliance Lead, IAM Admin, Orchid Admin).
02 Application Inventory
An incomplete application inventory is the #1 reason audits fail. Auditors expect a definitive list of every app in scope. The goal is to bridge the gap by automatically discovering unmanaged, shadow, and compliance-relevant applications.
(ISO 27001 A.5.9, NIS2 Art. 21)
- Managed applications inventoried via IAM/IGA systems.
- Unmanaged apps, with authentication /authorization, discovered by Orchid observability.
- Compliance-subject apps (PCI DSS, HIPAA, SOX, FedRAMP, NIS2), flagged by Orchid based on identity flows.
- Identity controls assessed per app: MFA, account lockout, password complexity, session handling, etc.
- Gap analysis generated, mapped to specific compliance requirements (incl. upcoming Quantum Safe controls).
03 Identity Lifecycle
Joiner-Mover-Leaver events are central to audit evidence. If accounts linger after an employee leaves or if access changes aren’t recorded, auditors call it out. Tracking the lifecycle events across both managed and unmanaged systems is key.
(NIS2, ISO 27001, FedRAMP AC-2)
- Joiner records: new accounts provisioned with role-based access.
- Mover records: access updated upon job/role change.
- Leaver records: timely deprovisioning across systems.
- Access requests and approvals are logged with timestamps.
04 Authentication Events
Proving how users log in, fail logins, and end sessions is now a compliance requirement (PCI DSS 4.0, ISO 27001, FedRAMP). Orchid consolidates authentication data into a unified audit log, ensuring nothing slips through.
(PCI DSS 4.0 Req. 8, ISO 27001 A.5.17, FedRAMP AC-7)
- Successful logins mapped to user + application.
- Failed logins tracked (frequency, causes, thresholds for lockout).
- Logouts/session terminations logged as proof of session management controls.
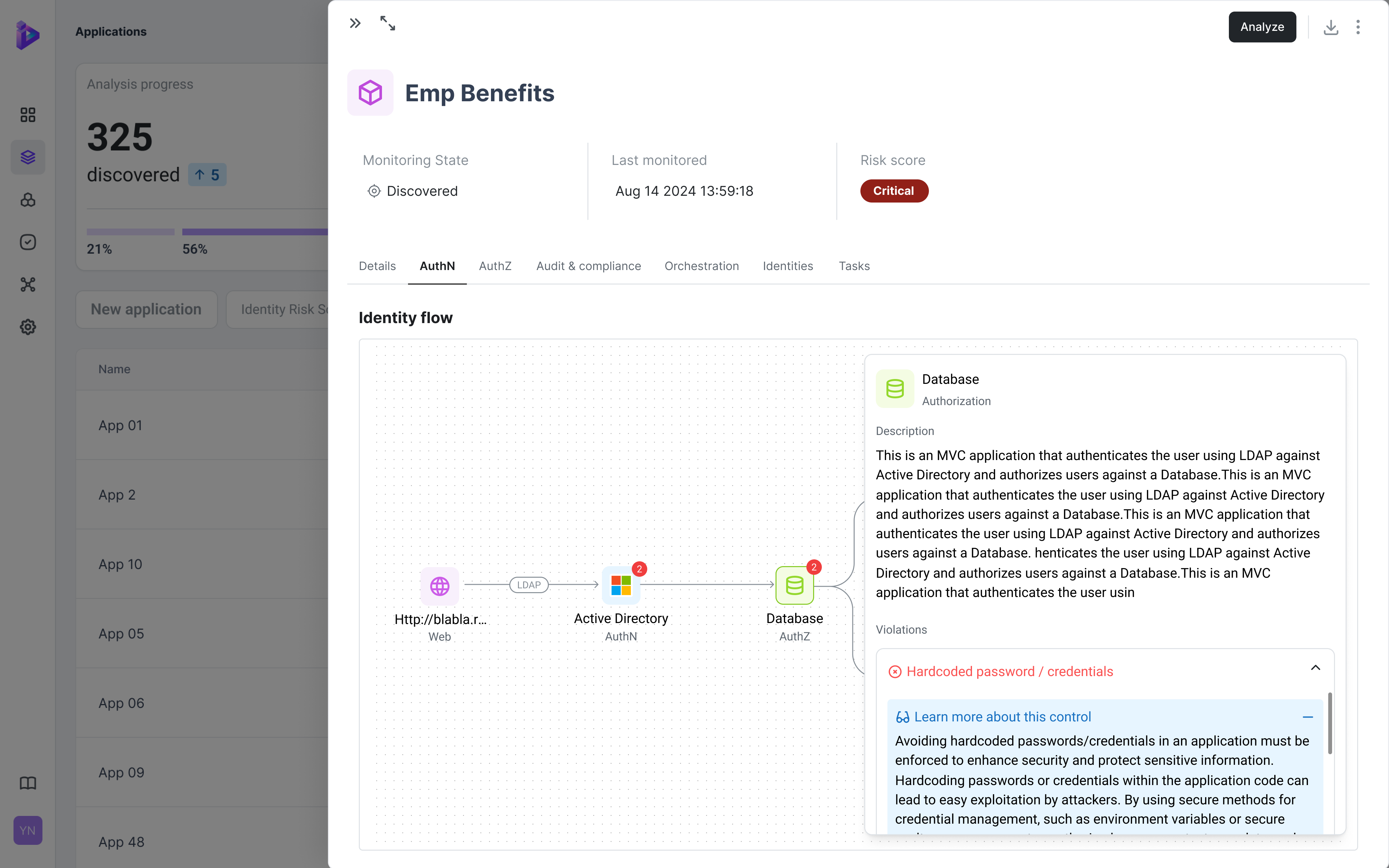
05 Access Governance
It’s not enough to claim “least privilege” - auditors demand proof. They expect evidence of role-based access, separation of duties, and logged privilege elevations. Orchid continuously validates governance controls across applications.
(ISO 27001 A.5.18, PCI DSS 4.0 Req. 7, FedRAMP AC-5)
- Least privilege enforced and provable.
- Privilege elevation events logged and approved.
- Separation of duties is evidenced (no critical functions concentrated in a single identity).
06 Orchid’s Overlay Audit Insights (Beyond Basics)
Auditors are raising the bar. They want visibility into hidden risks: orphan accounts, local credentials, over-provisioned users, and shadow apps. Orchid overlays these insights on top of traditional IAM evidence, closing gaps others can’t.
- Orphan accounts - active accounts without owners (ISO 27001 A.5.18).
- Local accounts - unmanaged system-level credentials (PCI DSS 4.0 Req. 7.2.5).
- Most-privileged accounts - admin/root usage across apps (FedRAMP AC-6, ISO A.5.18).
- Over-provisioned users - access exceeding business need (PCI DSS 4.0 Req. 7.2.1).
- Shadow applications - non-inventoried apps bypassing IAM (ISO 27001 A.5.9).
- Stale/inactive accounts - unused but active (FedRAMP AC-2(3)).
- High-risk activity patterns include repeated failed logins and off-hours access (PCI DSS 4.0 Req. 10.2, FedRAMP AU-6).
07 Audit-Ready Outputs with Orchid
Audits shouldn’t drain teams for months. Orchid turns continuous monitoring into exportable evidence: compliance-mapped reports, dashboards, and unified logs ready for auditors at any time. The result: faster audits, fewer findings, and lower costs.
With Orchid, organizations can provide auditors with:
- Always-up-to-date application inventory (managed + unmanaged).
- Continuous audit-ready evidence exports mapped to compliance frameworks.
- Unified identity audit logs across all applications.
- Risk overlays tied to PCI DSS, NIS2, ISO 27001, and FedRAMP.
- Compliance-based gap analysis highlighting missing/weak controls.
- Real-time dashboards showing identity compliance posture.
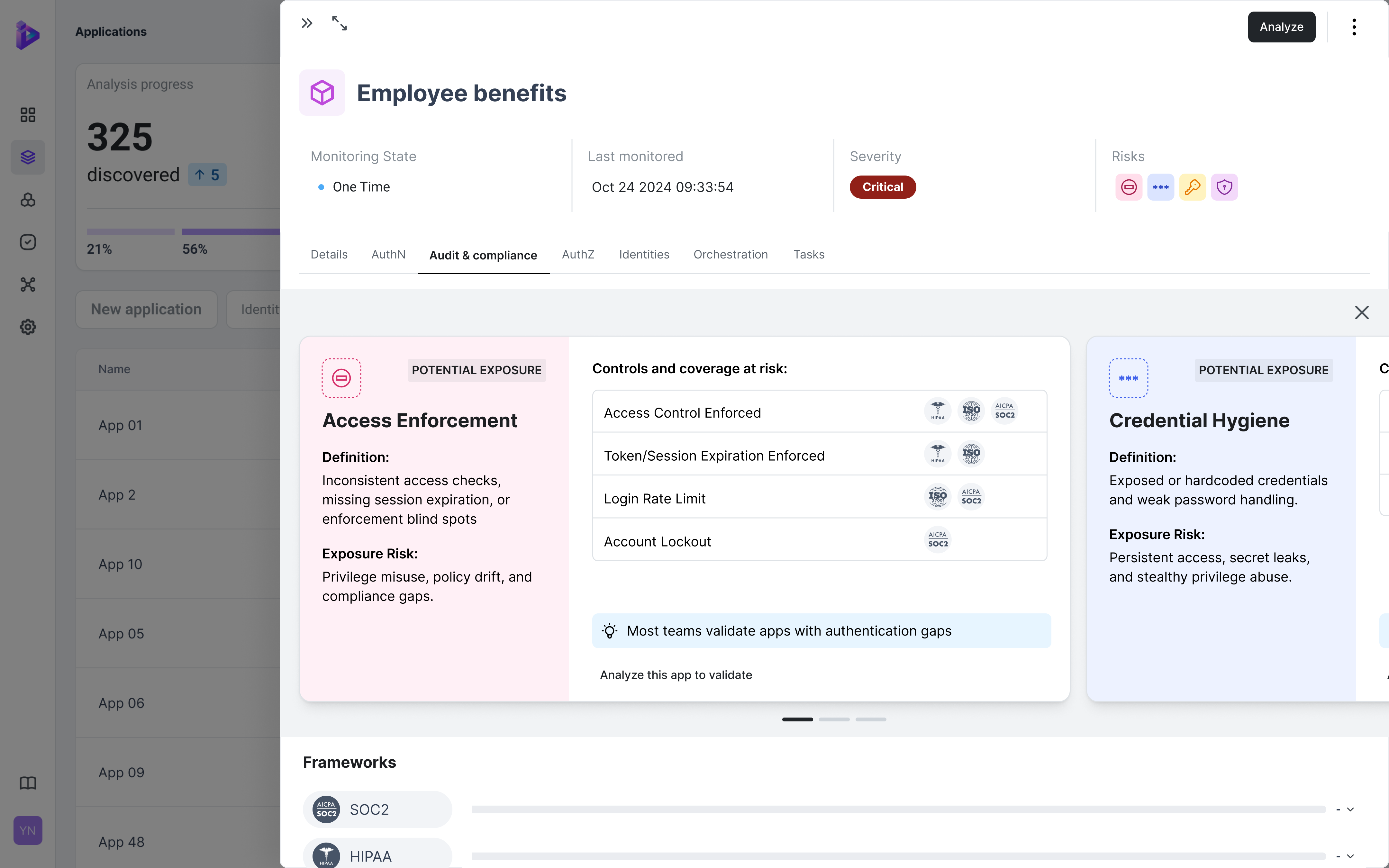

Understanding, let alone maintaining, identity security posture across any large organization- with its diverse and always evolving application estate- is a constant challenge.
Remember, that estate includes applications created by different developers, at different times- when technology, regulations and cyber risk were different- and even by different organizations if acquisitions were part of the growth strategy.
Any approach, but especially an automated one, that provides a comprehensive and accurate view into the true state of identity, is hugely valuable to CISOs. Especially when it can surface all of the identity flows coded in each application. We know that many threat actors are adept at finding the alternate or forgotten ways into our organizations, and this report highlights the most common exposures we need to look out for (and address).
The insights shared here are instructive for every cyber security professional.
- 48%
Storage of hard coded, cleartext credentials or use weak hashing
- 44%
Authentication paths that bypass the corporate Identity Provider
- 40%
A lack of baseline controls like rate limiting, account lockout and password complexity
- 37%
Outdated or non-standard authentication protocols
- 37%
of applications failed to enforce access controls fully or at all
Checklist to Identify the Top Missing Identity Controls
Download Checklist
Discovery and Gap Analysis: Continuous Visibility Beyond the Known
Orchid delivers continuous, telemetry-driven visibility into identity implementations across all automatically discovered applications regardless of geography, technology stack, or existing compliance knowledge. This capability empowers organizations to uncover both commonly missed controls and hidden identity mechanisms that conventional audits and reviews often fail to detect.
No Prior Context or Manual Input Required
Unlike traditional assessment and onboarding processes that rely on interviews, documentation, or involvement from app owners or developers, Orchid's analysis is entirely autonomous. It requires no prior data points, tribal knowledge, or manual onboarding, making it ideal for large, fast-changing environments.
Save Time, Save Money — Harness Your True Identity Landscape
By eliminating the need for human-led discovery, context-gathering, or code walkthroughs, Orchid significantly reduces the time and cost of identity posture management. It accelerates both discovery, gap analysis and remediation cycles including onboarding, freeing up security teams and engineering resources to focus on higher-impact work while utilizing the organizational siloed identity tools.
Checklist, Fully Covered
Our platform aligns directly with the Checklist to Identify the Top Missing Identity Controls and many more providing instant, actionable insights on where your applications stand and what needs attention.
- January 2025
PowerSchool Breach
Cybercriminals reportedly used stolen credentials to access a support portal that lacked MFA, exposing sensitive student and parent data.
- March 2025
Jaguar Land Rover Incident
A threat actor used stolen credentials to infiltrate the company’s Jira system, allegedly stealing over 700 internal documents.
- April 2025
Verizon Data Breach Investigations Report
Verizon Identifies Stolen Credentials as Top Breach Entry Point In their latest report









